security

Security runs through everything we do which is why we implement industry-leading, proven and comprehensive methodologies. Our approach to security is transparent and built to last.
Mugato has been instrumental in streamlining our infrastructure platform. Mugato made that process fast and safe.”
OUR ARCHITECTURE IS BUILT FOR COMPLETE CLIENT ISOLATION
When onboarding a new client, we create an entire dedicated data center in Azure. Azure SQL Database encrypts all traffic both at rest and during transport meaning there is no unencrypted traffic anywhere between our components. However, we give you the opportunity to use your own encryption keys rather than Microsoft’s.
UNIQUE ID (GUID) AND SERIAL NUMBER
Flexible geographic deployment options for multinational clients
UNIQUE AZURE DATA CENTER WITH DEDICATED COMPONENTS
Customizable backup retention (default 7days, extensible up to years)
INDIVIDUAL SERVERLESS FUNCTIONS AND RESOURCE GROUPS
Geographic backup replication options
SECURE KEY VAULTS FOR CREDENTIAL MANAGEMENT
Advanced encryption options, including client-managed keys
DEDICATED PAAS DATABASE
No multi-tenancy risks
UNBROKEN FOR 6+ YEARS AND COUNTING
Each year Mugato hires leaders in cyber security and asks them to have a go at our system to see if they can expose any vulnerabilities. Using different methodologies such as OWASP and NIST frameworks none of the companies that have investigated us managed to find any holes.
Penetration test methodologies:
installation
GETTING STARTED WITH MUGATO
Installing Mugato is a simple process that takes roughly 10 minutes during an online meeting. Mugato doesn’t come with an out-of-the-box appliance. Instead, we ask you to bring a clean virtual server created based on your trusted templates so you don’t need to verify tens of thousands of other files that might come with an out-of-the-box solution.
We installed Mugato and in less than one hour we were up and running, getting live data from our infrastructure. That was amazing!”
PRE-REQUISITES FOR A SMOOTH INSTALLATION
Whether you have thousands of servers all over the world or you’re a small enterprise with 100 servers in the basement, installation is simple.

HAVE A SERVER OR VIRTUAL MACHINE READY
SQL SERVER EXPRESS
NO ACCESS REQUIRED
Beyond the installation that takes less than 15 minutes, here's what to expect.
WHAT YOU’LL DO
WHAT HAPPENS IN THE BACKEND
Mugato Setup Process

INSTALLATION
GET YOUR FULL INFRASTRUCTURE BLUEPRINT IN TWO WEEKS
While most agent-based solutions take months or years to implement, Mugato gives value 14 days after installation. Mugato’s intelligent process mining algorithms can map out most of your IT environment after running for only a couple of weeks so our clients can consolidate infrastructure, implement micro-segmentation, right-size, reduce IT costs, and de-risk operations.
RUNTIME

A UNIQUE SOLUTION FOR INFRASTRUCTURE MANAGEMENT
Built from 25+ years of solutioning and implementing enterprise infrastructure.
AGENTLESS ARCHITECTURE
ISOLATED AND CONTINUOUS
HIGHLY SECURE
runtime
Mugato compared to industry standard solutions
features
mugato
OTHER SYSTEMS
Data collection

GIVING YOU A HOLISTIC OVERVIEW WITHOUT INTRUDING
Mugato's intelligent process mining algorithms only collect meta information regarding your enterprise's infrastructure which is why it doesn’t require high privilege accounts or access. We don't collect or process any personal or company data and never will.
data collection
DATA SECURITY AND COMPLIANCE IS WHY WE BUILT MUGATO THE WAY WE DID
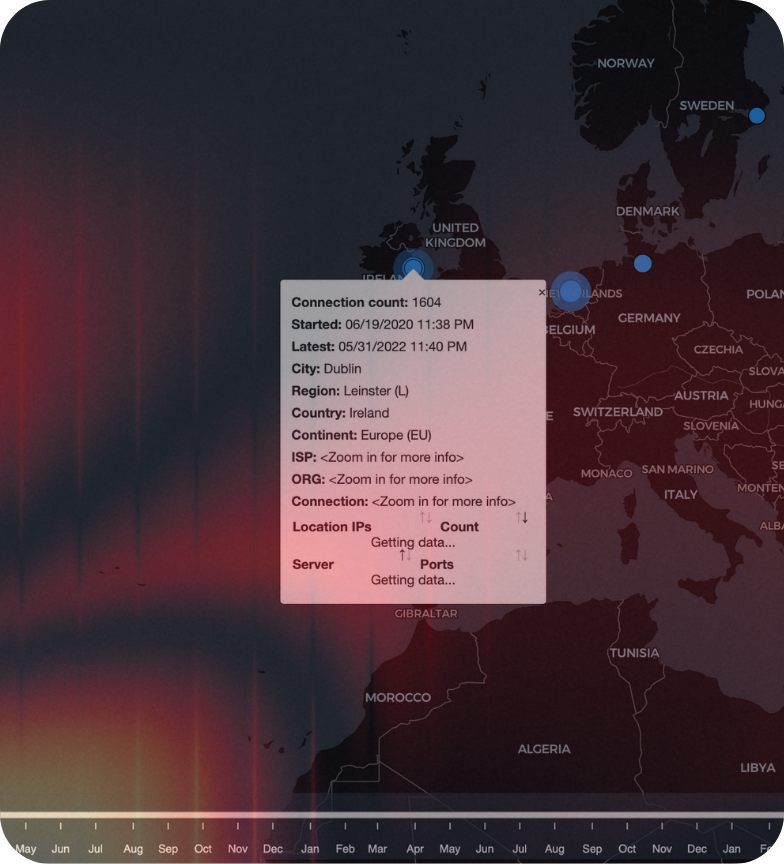
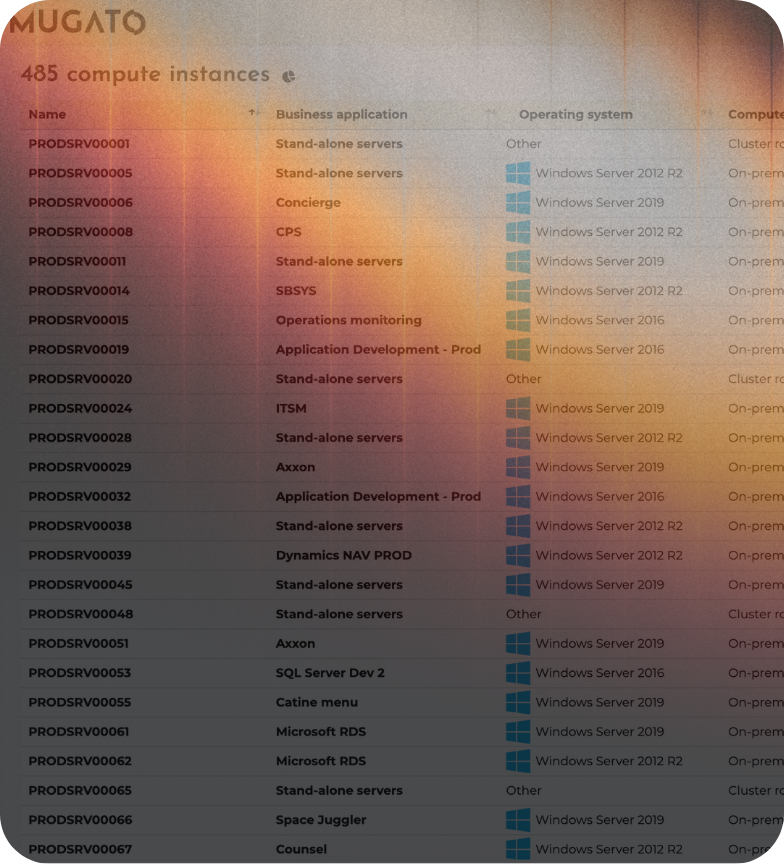
DATA COLLECTION
We don't process any personal or company confidential data at any point. The credentials that our collectors run on don’t allow them to collect any such data on most operating systems. The information gathered is basic metadata about your IT infrastructure such as:
SECURITY AND PRIVACY
Our security architecture prioritizes client safety at every level. Security is fundamental to everything we do, which is why we implement the latest and most-proven methodologies. Our transparent approach to security has earned high praise from industry experts. With complete client data isolation at its foundation, our architecture incorporates a multi-layered approach to security.

AI COMPLIANCE
Unlike other AI tools that rely on generative approaches, Mugato uses predictive and causal AI powered by deterministic meta information from a clients' servers. This ensures trustworthy, fact-based results without statistical guesswork.
Since we only collect meta information and avoid both generative AI and processing of personal or company identifiable data, our solution fully complies with data protection and AI regulations.

